Protect Your Customers Against
Stop Automated Attacks Against Your Web Apps and APIs.
MirrorTab gives you control to turn off automation in critical workflows, ensuring only real users can access your web apps and APIs.

Block Bots. Prevent Fraud. Stop AI Automation.
Automation is the attacker’s primary weapon. Bots, fraud tools, and Agentic AI target logins, transactions, and APIs. MirrorTab shuts them off at the edge using the stack you already have in place.






Account Takeovers
Concurrent Session Exploitation
Content Scraping
Automated Money Movement
Transaction Fraud
Malicious Browser Extensions
Cookie and Token Theft
Formjacking
API Abuse
Data Leakage
AI-Powered Bots
Data Harvesting
Script Injection
Agentic AI attacks
Untrusted Device Access
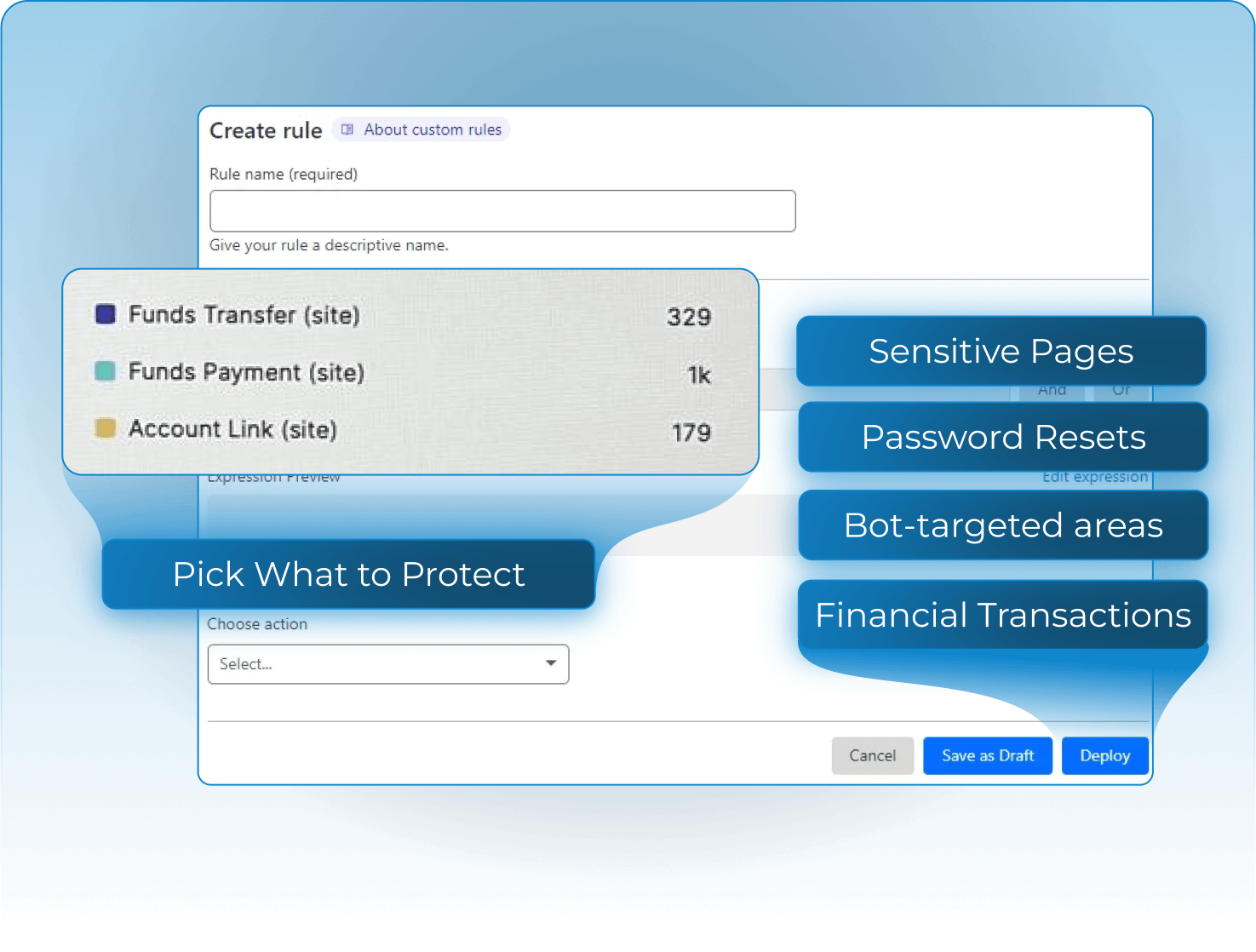
Automation Defense Without the Friction
MirrorTab extends your existing edge stack (CDNs, WAFs, and fraud platforms) to block bots, fraud automation, and Agentic AI before they can exploit your applications.

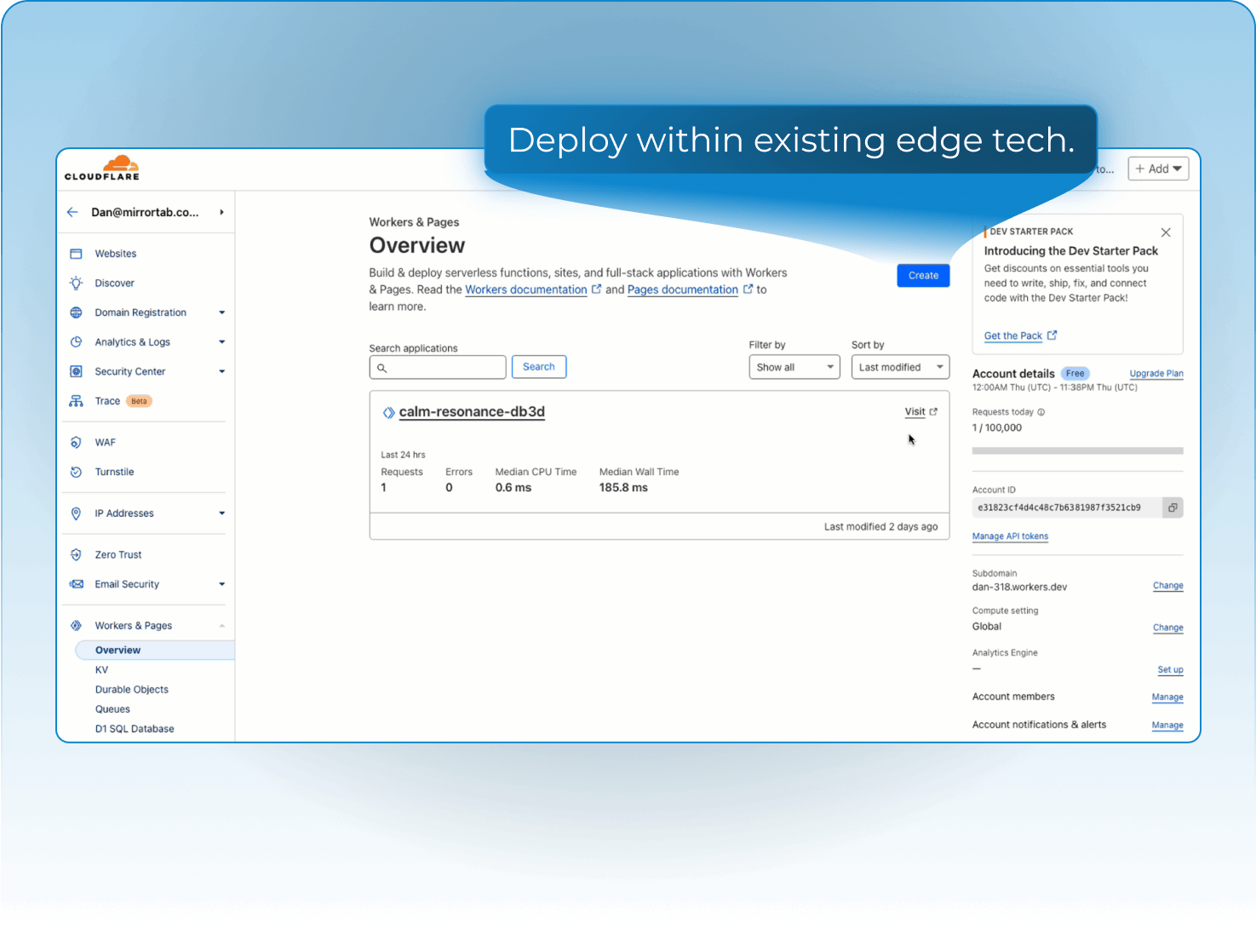
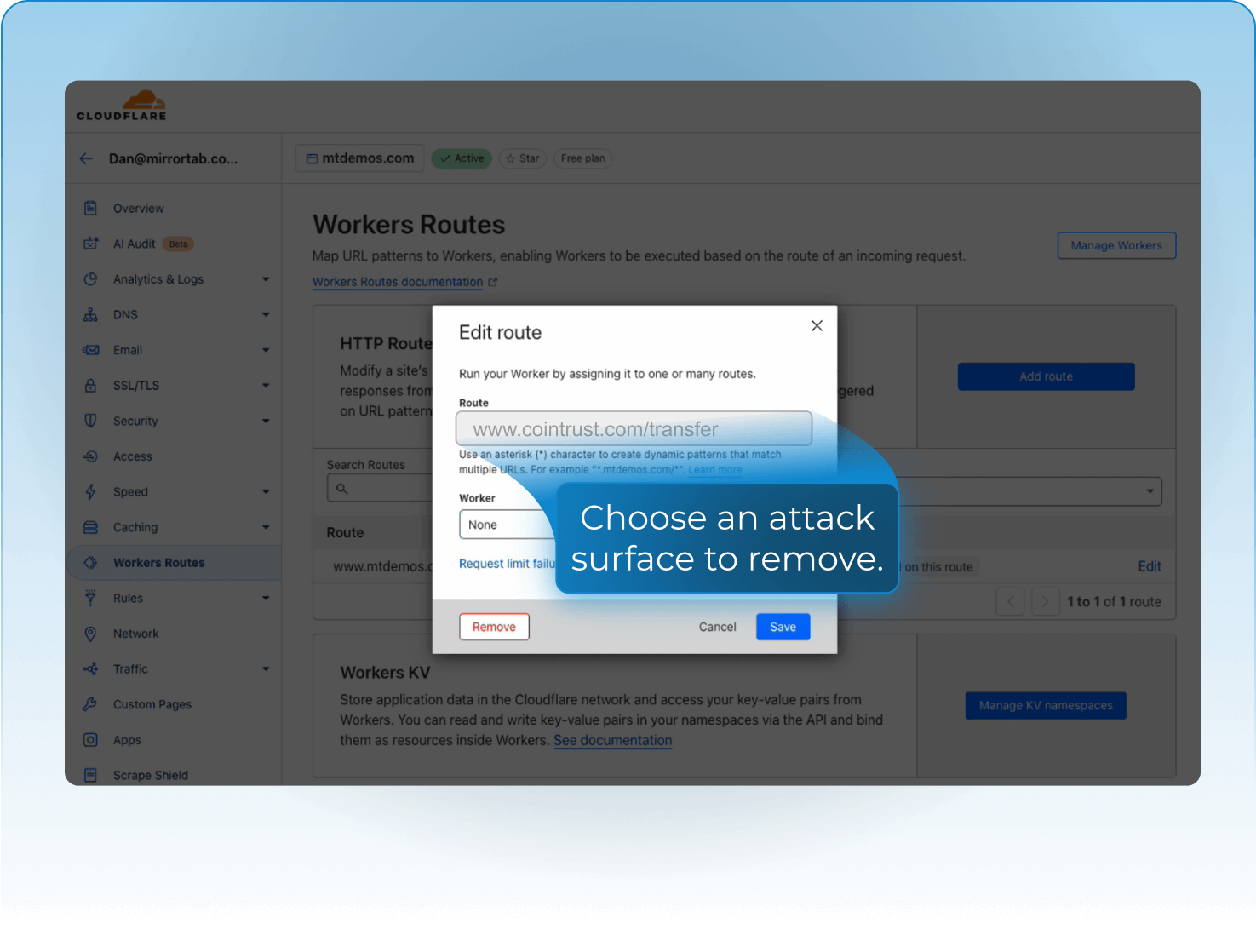
How MirrorTab Works
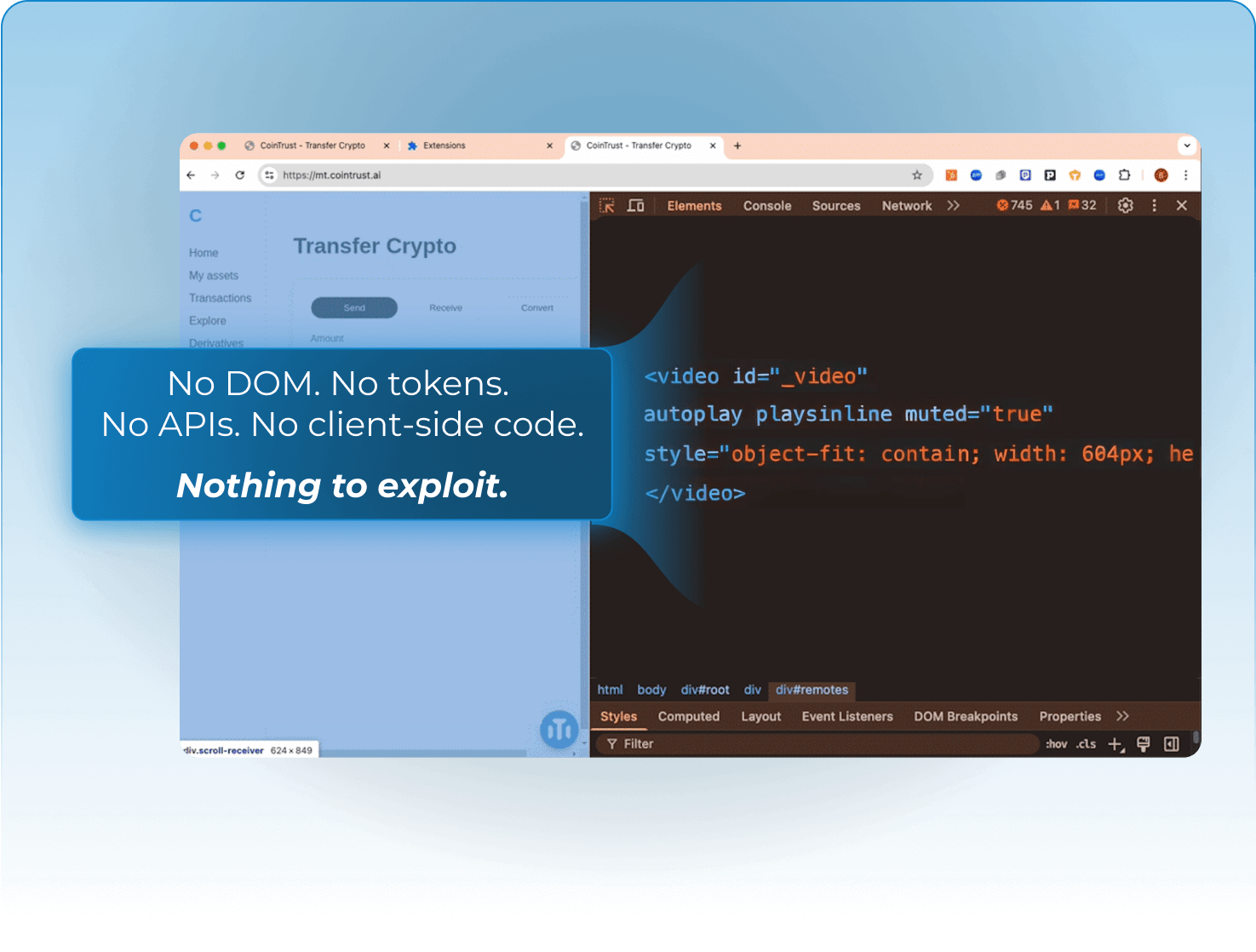
No DOM exposure
Your app’s code, APIs, and data never touch the end-browser.
No data leakage or fraud
Even compromised devices can’t leak sensitive data.
No plugins or agents
Fully edge-driven. No code changes. No user installs.





Triggers via WAF, bot score, auth state, or feature flag.
Fully server-side. No code. No customer installs.
Works with any edge platform (CDN, WAF, etc.).
Breakthrough performance. Nothing else compares.
Your Web Apps and APIs. Fully Protected. Zero Automation.
MirrorTab ensures your applications behave as intended. Content loads accurately, workflows run seamlessly, and performance stays strong even in low-bandwidth environments.

Improves performance over low bandwith connections.



*Example using a web content heavy site.




How MirrorTab Compares
Other tools detect or slow automation. MirrorTab turns it off completely.






The Story Behind MirrorTab

MirrorTab was founded by the CTO and co-founder of Honey (acquired by PayPal).
.png)
At Honey, we built the world’s most popular browser extension by working deep in the DOM.
Now, we’re flipping the model—removing the DOM entirely to stop automation from bots, fraud, and Agentic AI.









.png)